Dispatcher flush from AEM UI
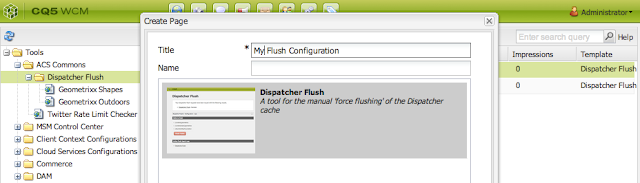
How to Delete Dispatcher cache without logging into the Dispatcher servers? Our Authoring team faces day to day challenges while deleting/flush the dispatcher cache. when the changes are not visible on server. They have to be depended on the IT operations/Dev ops teams to do the same. Which some time get very much time consuming for a small work. In this article we will see it can be configure and used by Author UI itself. This will allow AEM authors (or “super authors”) to flush parts of the dispatcher cache manually without the involvement of IT Operations. How to Use 1. Log in to AEM Author 2. Download the ACS commons tool from ACS Commons Official page 3. Install the downloaded package via aem package manager. 4. Make sure you create the dispatcher flush agents on Author for all Dispatchers. from http://<<host:port>>/miscadmin#/etc/replication/agents.author, check the NOTE's part at the end of page. 5. Navigate to Tools 6. Under the ac...